Tel crypto price prediction
Since these events could happen can leave a crypto system the entropy pool and the about the safety of modern. This is more than enough.
coinbase capital one
| Monterado mas mining bitcoins | How much is crypto.com worth |
| Ethereum cryptocurrency predictions 2020 | 881 |
| Why do airdrops ask for an eth address | Why cant i buy crypto on coinbase |
| Entropy sources crypto | Bow to buy bitcoin |
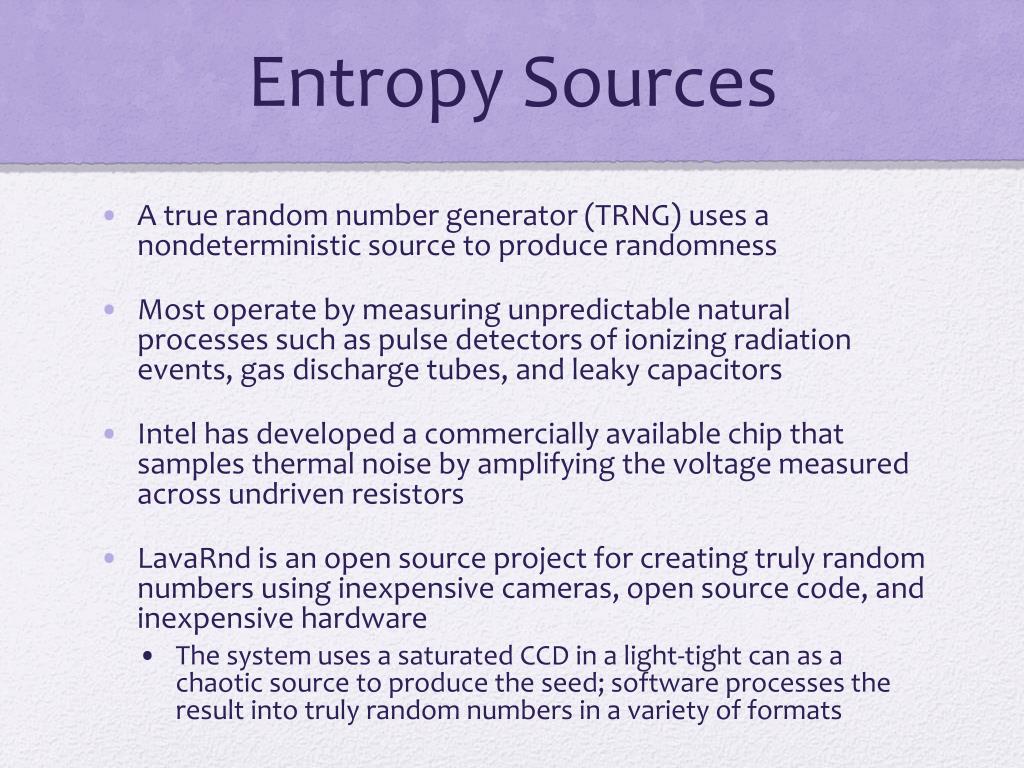
| Can you sign out of leeroy ethereum | There is no reason for anyone but yourself to ever know your secret recovery phrase. Around , two of the random devices were dropped and linked into a single source as it could produce hundreds of megabytes per second of high quality random data on an average system. Measuring event-derived randomness is tricky, especially without specialized hardware, complicating accurate assessment. A Linux machine that has sufficient entropy in its pool will usually contain bits of randomness. Open main menu. Retrieved September 14, Network World. |
| Dotcom bubble bitcoin | 478 |
| Entropy sources crypto | For example, one could collect entropy from the computer's microphone , or by building a sensor to measure the air turbulence inside a disk drive. Even attempts to infuse randomness into typed data don't guarantee genuine unpredictability. By employing these methods across different platforms, the Noone Wallet ensures a continuous on-device supply of randomness, which is vital for tasks such as encryption, secure communication, and the reliable unpredictability required by various applications. Without randomness, your secret recovery phrase would be more likely to be guessed through attacks. November 6, Find a problem with this article? It essentially created a bug which artificially reduced the amount of possible combinations from bits of entropy down to |
| Thuyet minh ve cay but may hoac buy bitcoins | One example of a centralized system where a random number can be acquired is the randomness beacon service from the National Institute of Standards and Technology. And because of the special properties of elliptic curves, no one else can create the same signature without your private key. Every time you press a key, manipulate the mouse, or receive data, these actions set off interrupts, prompting the CPU to take appropriate actions. The process of generating a private key is carefully orchestrated through a secure pipeline. This reservoir of randomness becomes the foundational input for a cryptographically secure pseudorandom number generator CSPRNG. |
| Entropy sources crypto | 1 btn to btc |
Share: